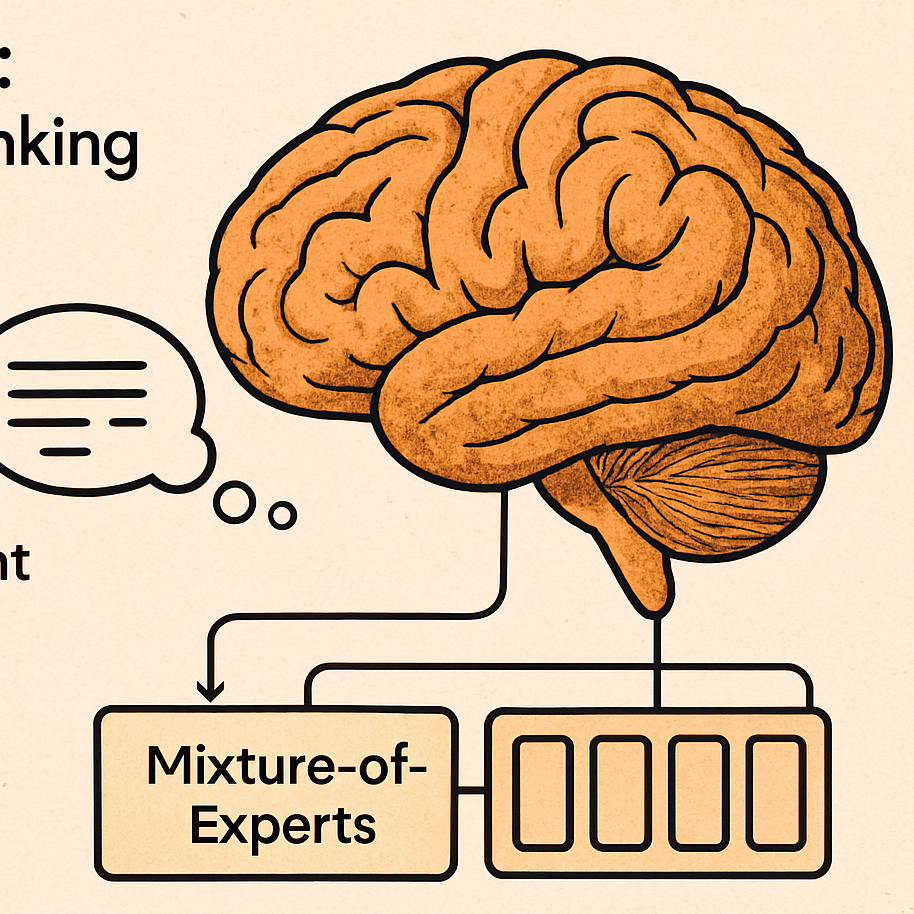
DeepSeek R1: Unveiling the Thinking Process of an Advanced LLM
A deep dive into how DeepSeek R1 'thinks' – exploring emergent reasoning, structured chain-of-thought training, lossless long-context handling, and a Mi...

Part 1: Envisioning the Next Evolution in Robotics with Generative AI
The intersection of robotics and Generative AI heralds a transformative era, redefining capabilities and introducing levels of adaptability previously c...

Enhancing SSH Security with config files and Passphrases
Explore the advanced practices of SSH key management and security, focusing on the use of `~/.ssh/config` for seamless yet secure access management and ...

Unraveling AI: Latent Spaces and the Power of Emergent Properties - A 2024 Perspective
Dive into the heart of AI innovation, where the mysteries of latent spaces and emergent properties unlock unprecedented problem-solving and creative pot...

Understanding the Evolution of AI: Transformer Models vs. Traditional Deep Learning - A 2024 Perspective
The realm of artificial intelligence (AI) has seen remarkable advancements, particularly with the rise of transformer models. As we step into 2024, let'...

Harnessing Generative AI in Cybersecurity: A Strategic Approach
Exploring the transformative potential of Generative AI in cybersecurity, from real-time threat detection to enhancing threat intelligence and automatin...
